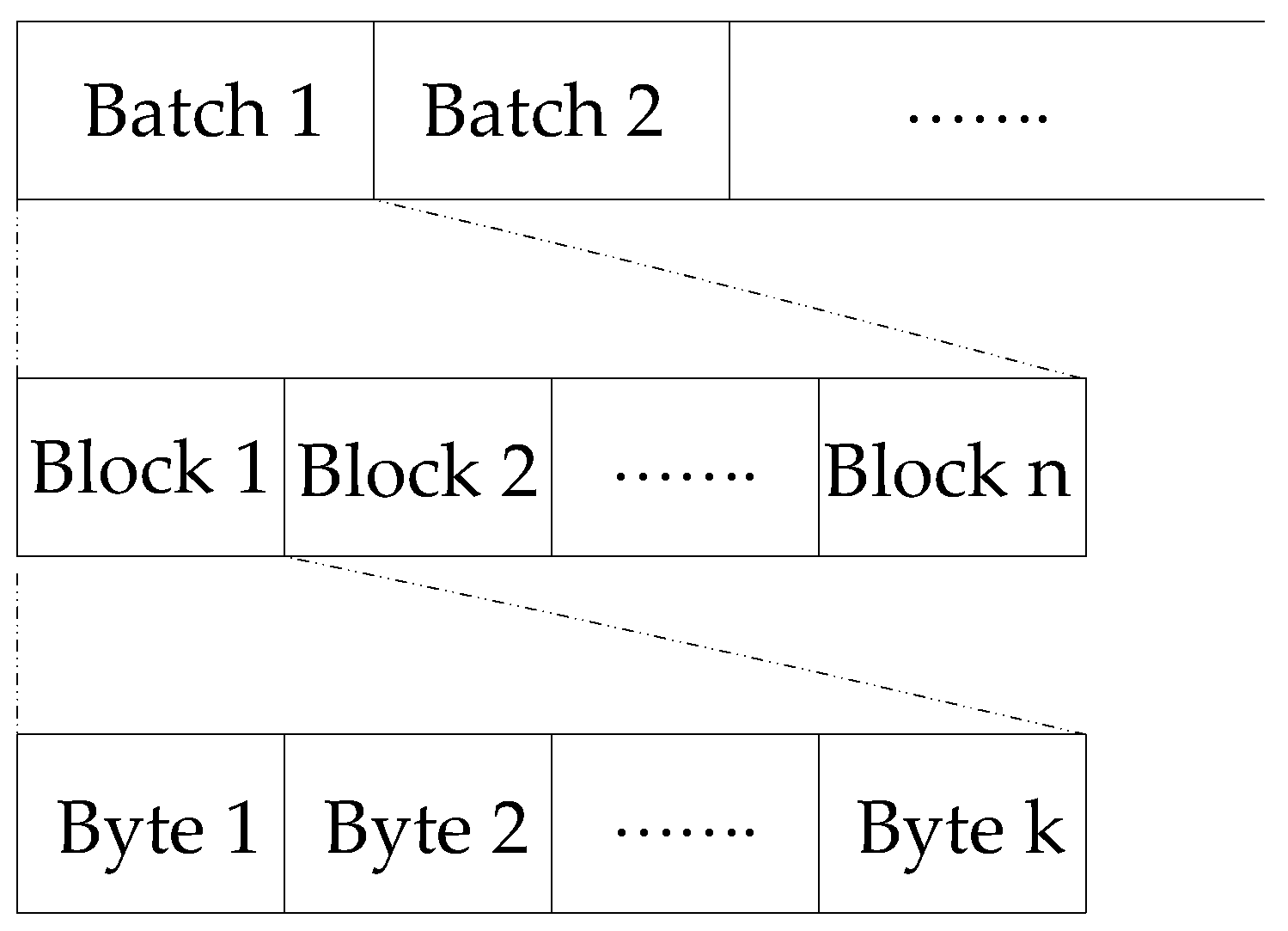
Admission Configuration - CloudCampus Solution V100R020C00 Design and Deployment Guide for Multi-Campus Network Interconnection - Huawei

Pie-com Ihr Brodit Online Distributor. WLAN SMART HOME 6 STÜCK SMARTES HEIZKÖRPERTHERMOSTAT + WLAN GATEWAY von Fontastic
Future Internet | Free Full-Text | Protecting Sensitive Data in the Information Age: State of the Art and Future Prospects







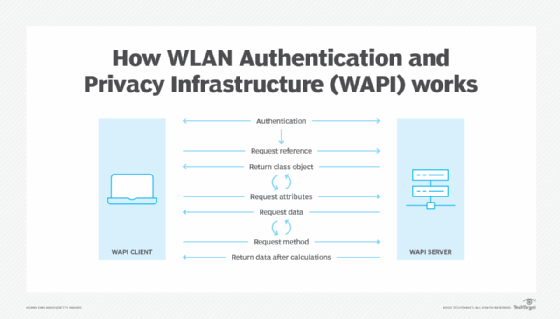


:quality(90)/p7i.vogel.de/wcms/2d/45/2d45d0e00fba1542d0185aa9b78102dc/0111642144.jpeg)